TIM8 Base
Basic functionalities of the TIM8 Server
All modules are based on the TIM8 Base Server, which can be reached via a modern WebGui and is multilingual (DE/EN) (other languages on request). The monitoring of the server is done via SNMPv3 and a flexible role and rights system for end users, application users and administrators allows the secure use in all conceivable scenarios. All other modules are based on a flexible licensing model, where the customer can individually determine the number of licenses and required modules.
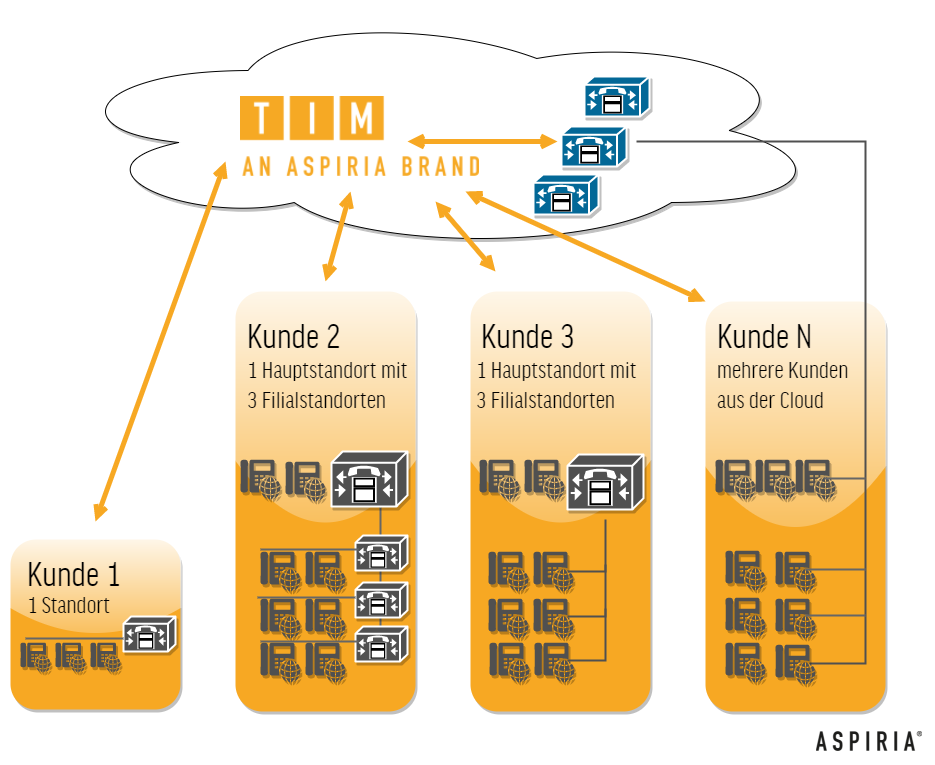
The use of TIM in multicluster environments is possible as well as the parallel administration of Cisco Unified Communications Mangers of different versions. For rollout and operation, all commercially available data sources (AD, LDAP, SQL, CSV file, etc.) can be used with the option of permanent synchronization.
MULTI-CLIENT CAPABILITY
Multi-client capability (XMPP / SMTP per client, assign licenses per client), no limitation in the number of groups, group images. The multi-client capability is based on a role-based rights concept, which makes it possible to assign freely definable roles and rights to freely definable groups and participants. This feature is the basis of all modules and functions of TIM8.
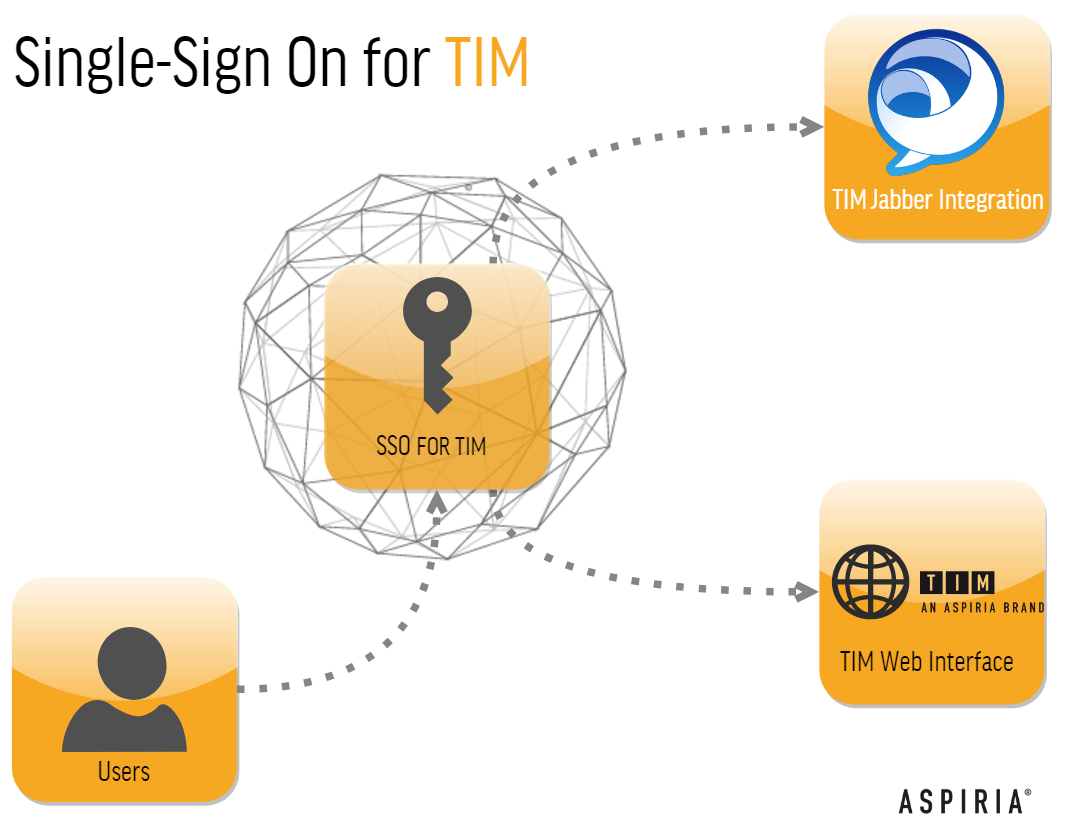
SINGLE SIGN ON (SSO)
With the single sign on feature of TIM8 it is possible for users to log on to TIM8 and their Jabber client directly after logging on to their PC once without having to enter login information again.
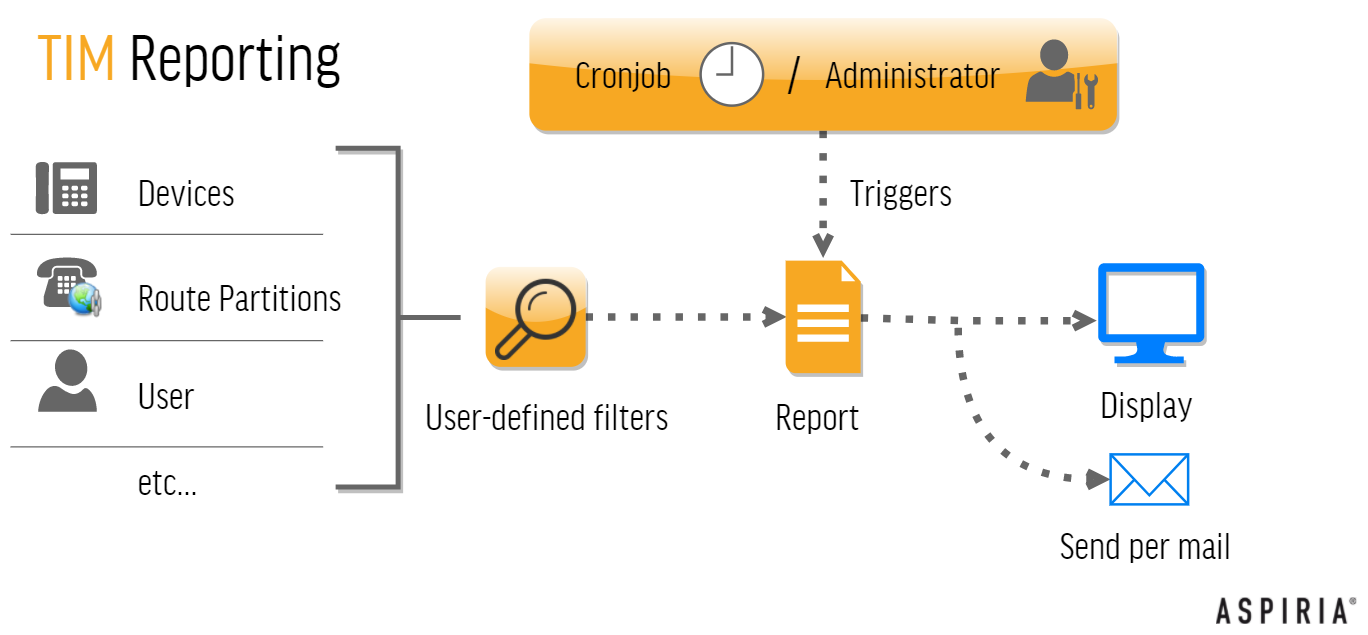
REPORTING
With TIM8 Reporting, reports can be created from the data available in TIM8. The data sets, search parameters, parameter names, order as well as sorting are freely selectable. Furthermore, reports can be created automatically via the cronjob/scheduler module. With recurring execution e.g. daily updated inventory lists or number directories can be created. The rights system of TIM8 ensures that one can generate a client-capable and audit-proof reporting.
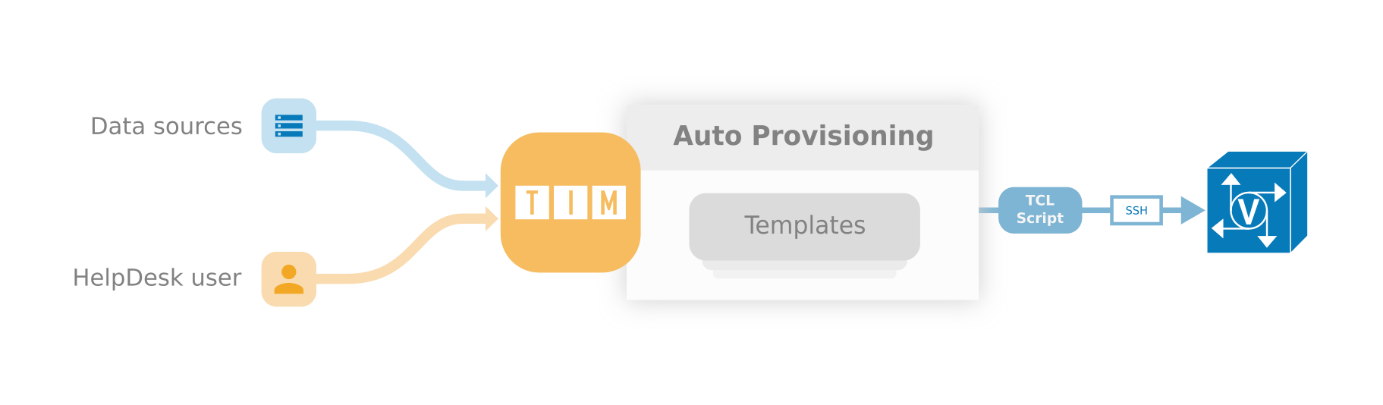
TCL ENGINE (AUTO PROVISIONING REQUIRED)
The TIM8 TCL Engine can be used to manage additional network components via processes. Examples are port changes at switches or configuration changes at SRST routers. The TCL Engine can access all systems (manufacturer-independent) that can be administered via a console access.
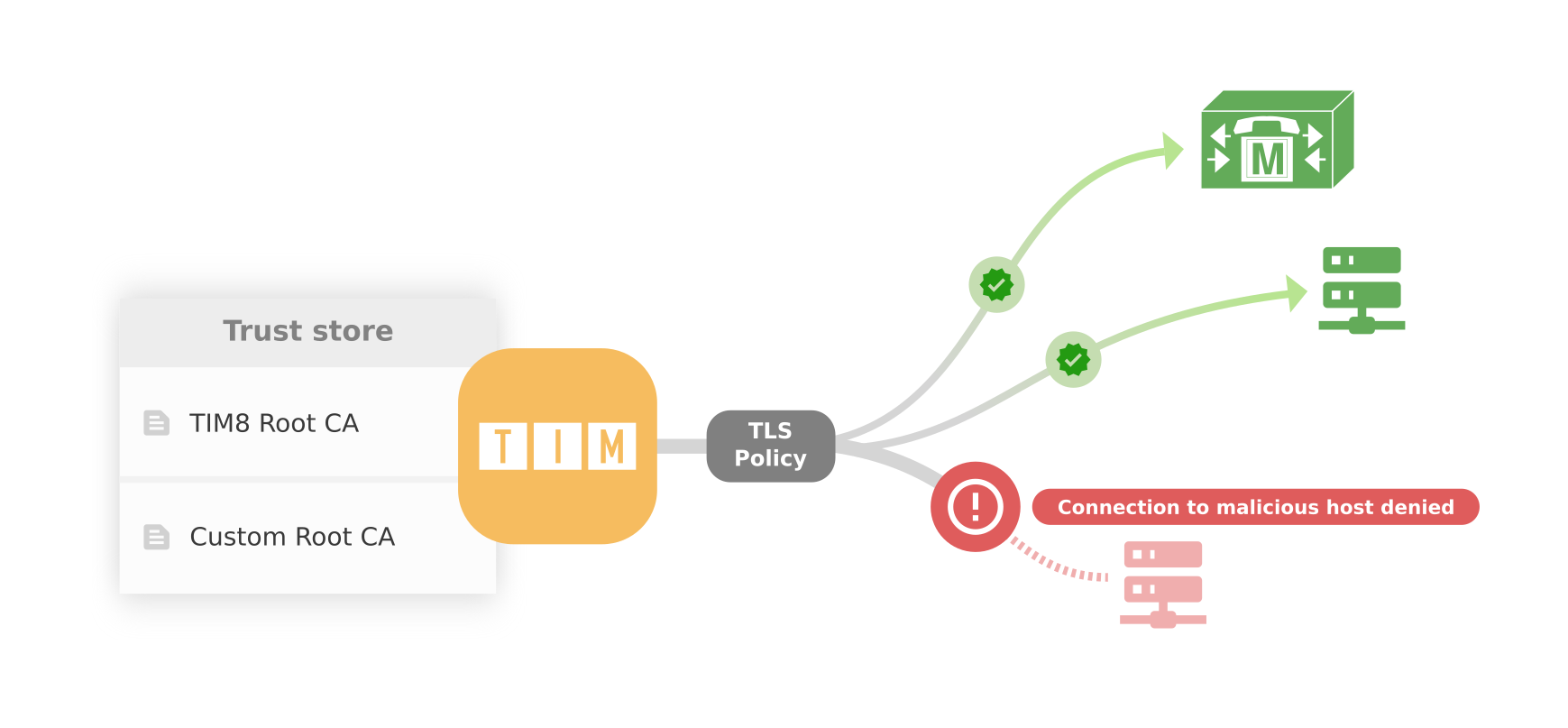
CERTIFICATE MANAGEMENT, TLS (NONE / BASIC / STRICT)
With the integrated certificate management, certificates can be administered and the setting of security levels for communication with other systems can be managed.
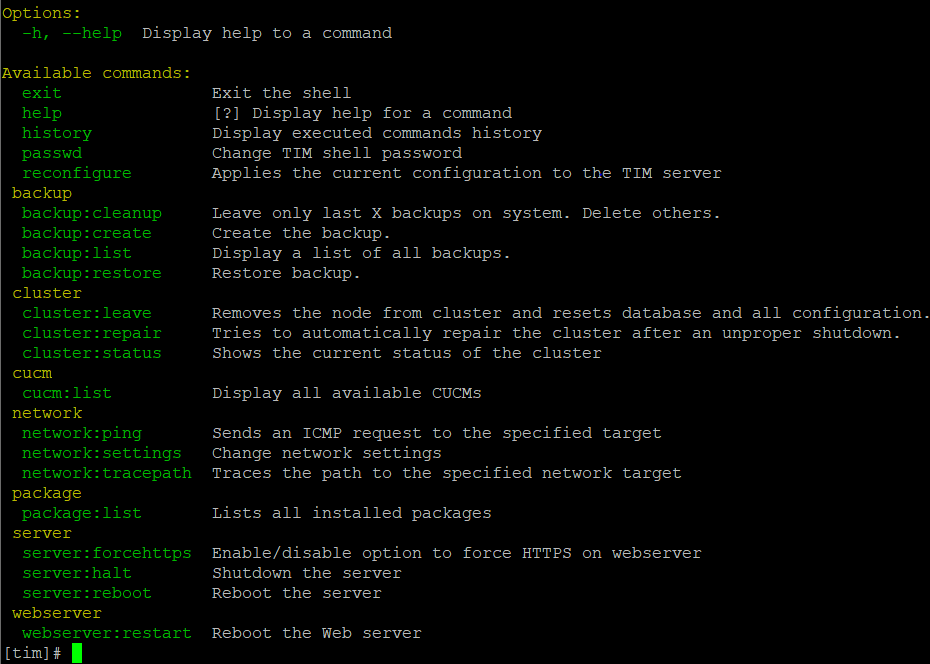
TIM SHELL
The TIM Shell is intended for the initial installation and for emergencies when you do not (yet) have access to the graphical user interface (GUI) of the TIM8 server.
The TIM Shell uses the usual command line input with parameters to make basic configurations. Additionally the TIM Shell provides some tools for error diagnostics e.g. for backups, cluster operation and network.
LOCAL ADMINISTRATORS FOR MULTIPLE GROUPS
TIM8 provides local administrators that can be created independently of CUCM or AD users and exist exclusively in the TIM world. This allows extensive use in shared environments and outsourcing projects.

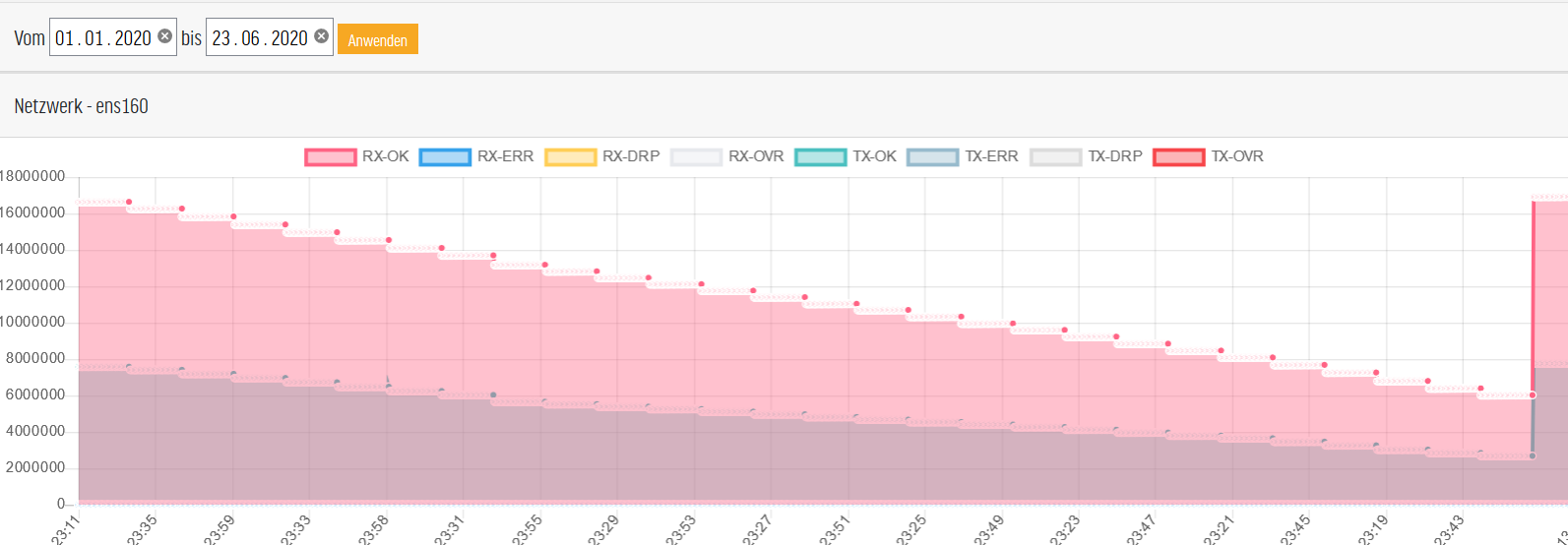
PERFORMANCE STATISTICS
For use cases where no central monitoring via SNMP is available, TIM8 provides extensive performance statistics. From the data throughput of the network cards to the utilization of the server CPUs, administrators can obtain information about all system parameters at any time.
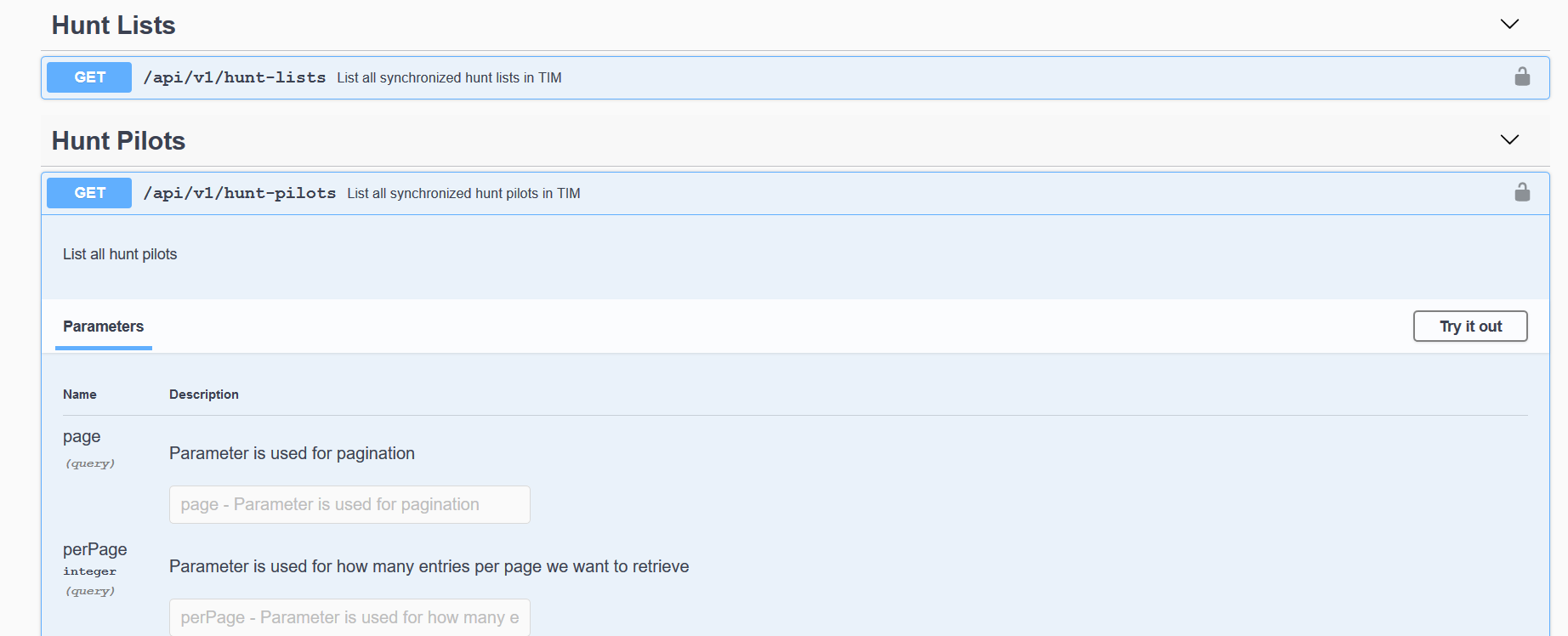
TIM8 REST API -ACCESS TO THE CISCO UC WORLD
TIM8 is the first product on the market to offer a REST API that allows third-party systems (e.g. ITSM systems like ServiceNow) to retrieve relevant data for advanced processes from the CISCO UC world. This is done in real-time, fully documented and based on the quasi standard Swagger.
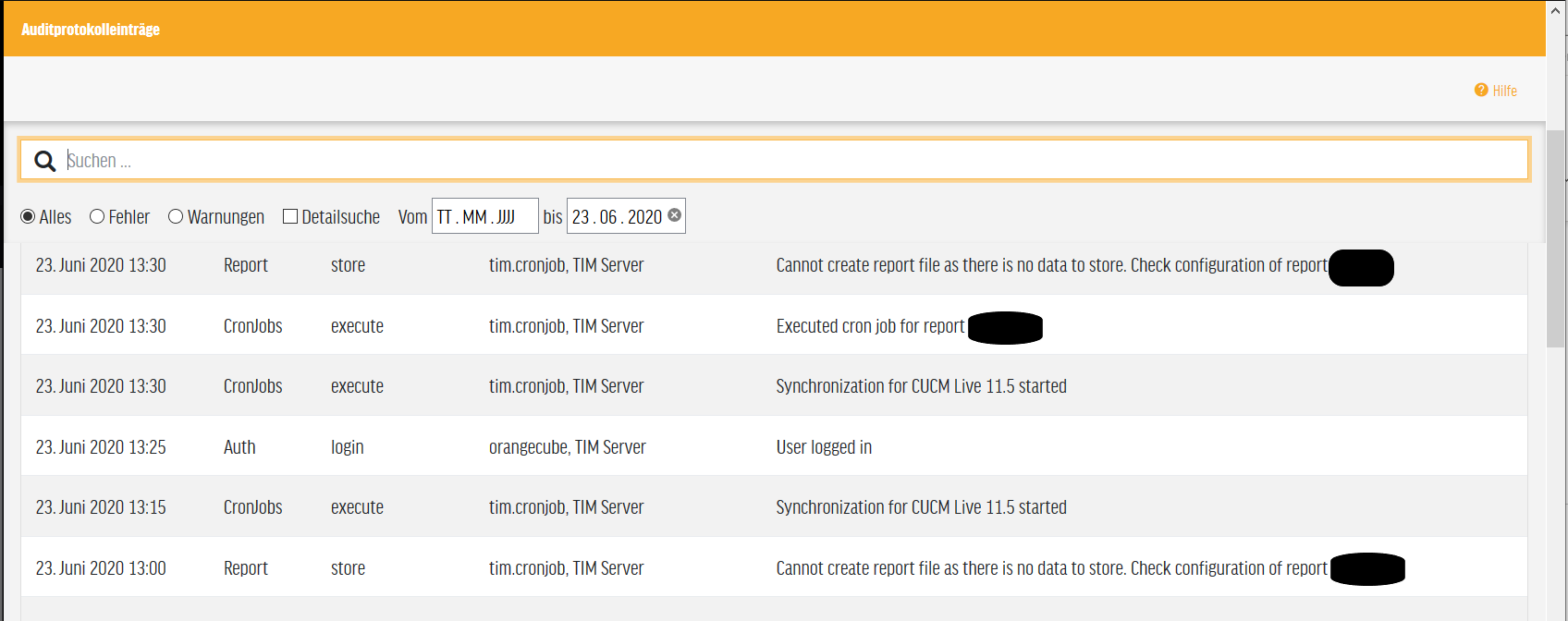
AUDIT-PROOF AUDIT LOG
Audit-proof audit logs are indispensable in both medium and large environments. TIM8 contains a complete record of all actions on the TIM8 server, in the TIM8 cluster and with all connected external systems. Since the records can also be searched in detail, irregularities on the TIM server or in the communication with third-party systems can be discovered quickly and errors can be corrected immediately.